| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |

Two core developers of dSploit went separate ways in the fall of 2014. dSploit’s father merged it into the commercial zANTI 2 with ambition to build a series of security apps on Android platform. Meanwhile, the other founder (now cSploit‘s father) can’t wait the distant promise to open source of zANTI 2. Thus, he decided to fork the killed project and finish all the original dSploit To-Dos on a new core – cSploit, by himself.
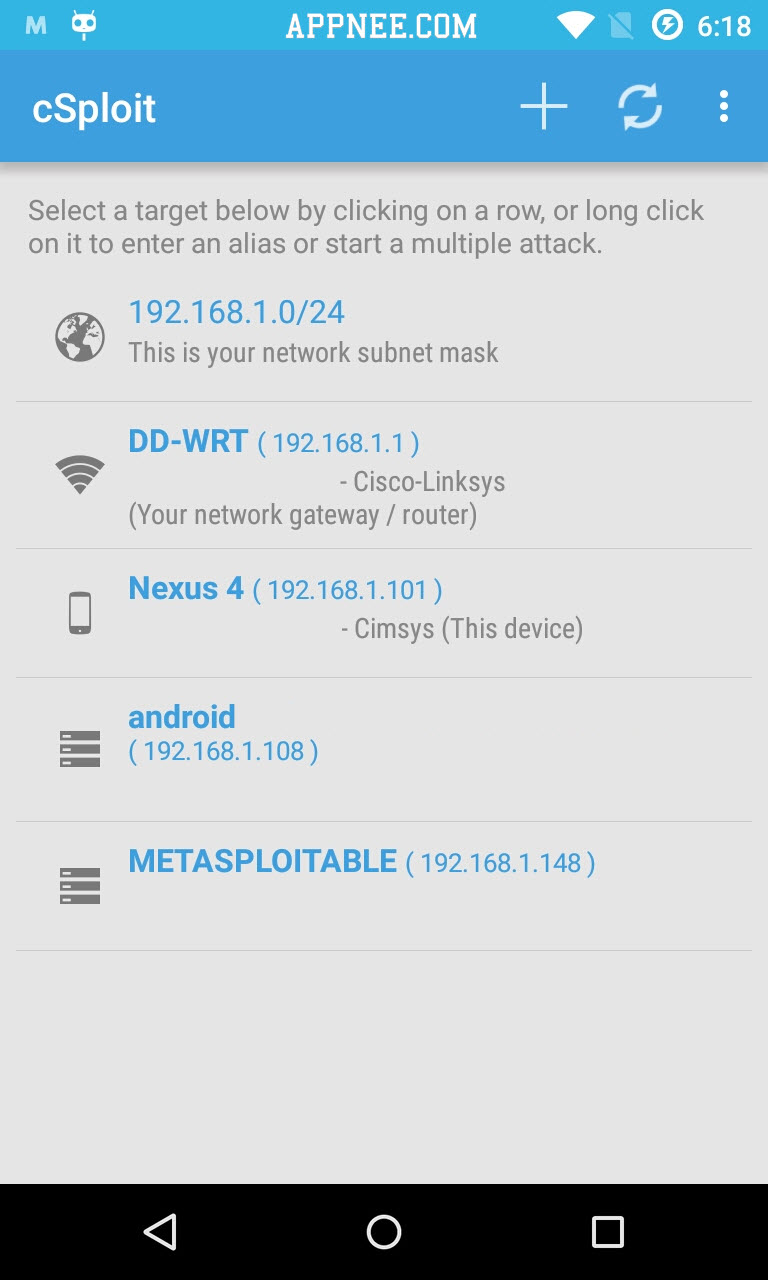
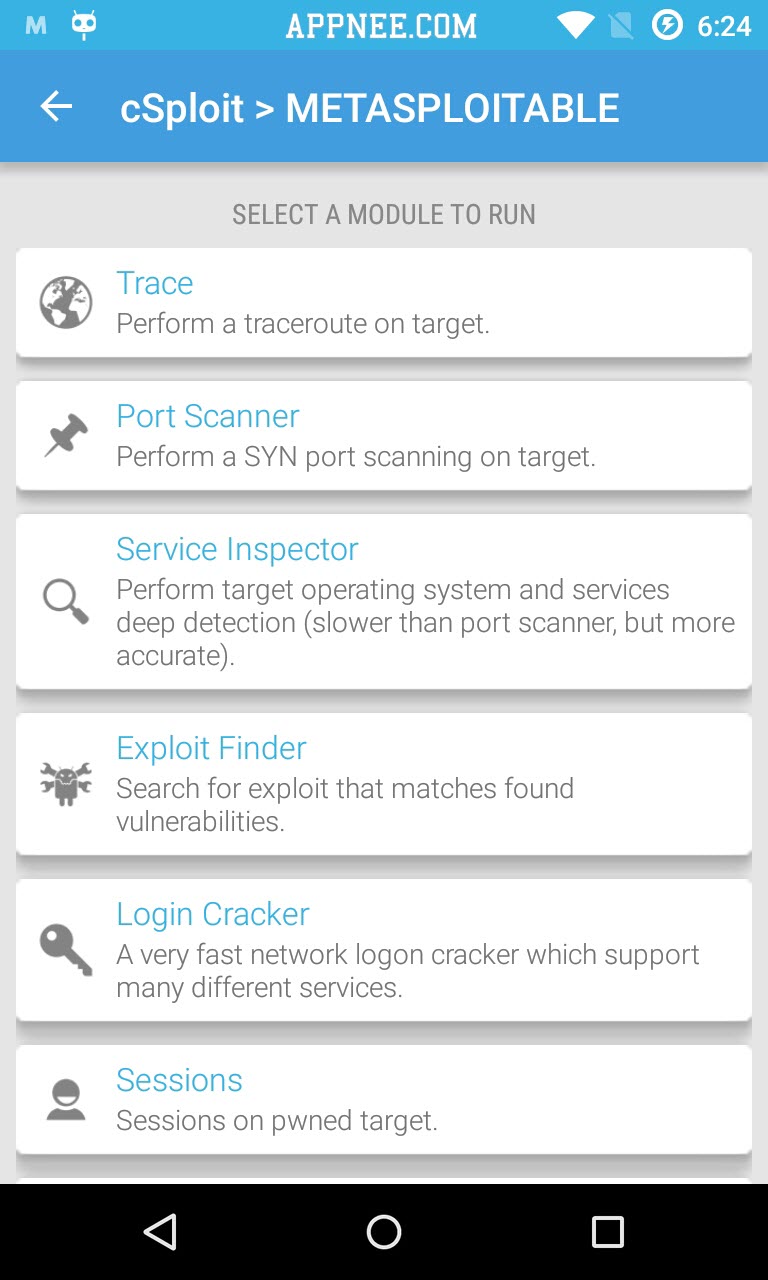
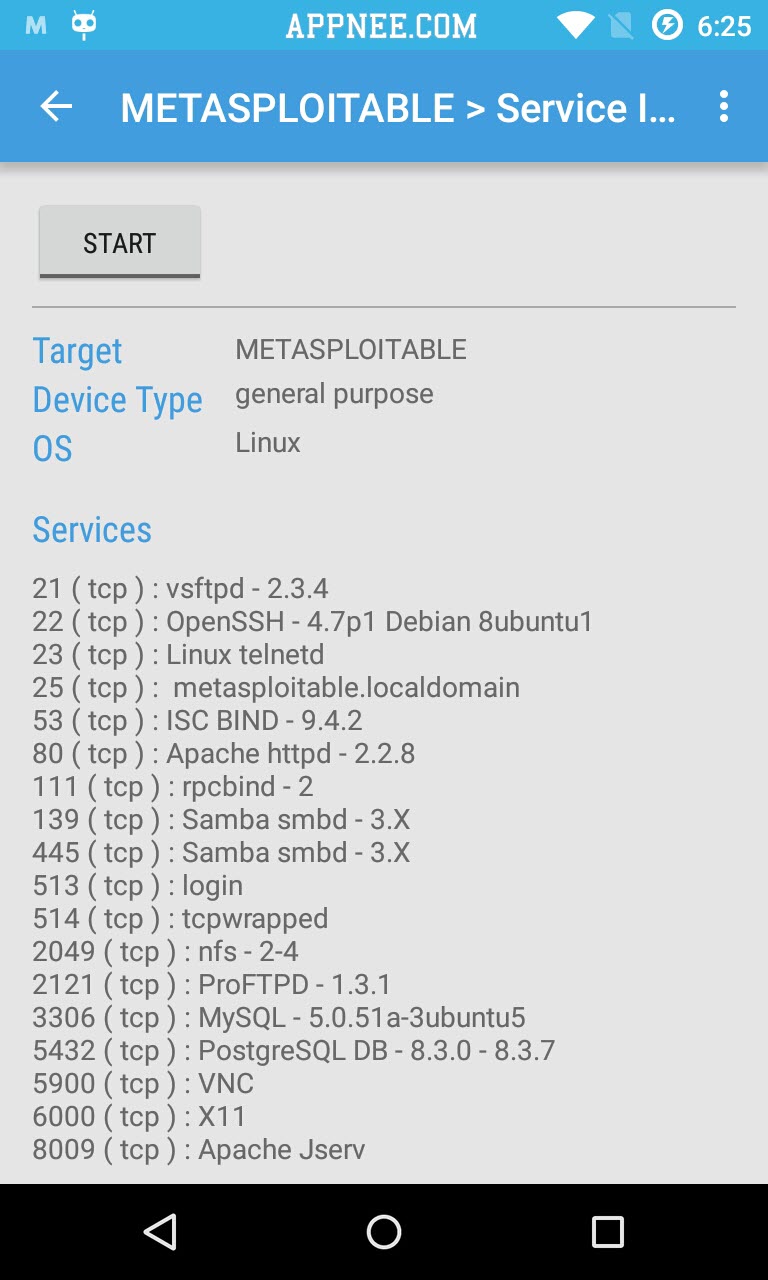
No doubt, as successor of dSploit, after adding a lot of new things, cSploit has become currently the most complete and advanced network security analysis and penetration professional toolkit on Android. The biggest change in cSploit is abandoned the old way and adopted a more effective new core to work. In other words, you will find that it runs faster. In short, cSploit enables you to scan all devices in a network, such as smartphone, laptop, and to recognize their operating system, running services and open ports for deeper penetration test. All this will be finished on your smartphone with Android OS.
BTW, By reading the core source code of dSploit and cSploit, you will find that their basic code is the same, and their core functions are all based on other excellent open-source apps, such as: arpspoof/ettercap/tcpdump/hydra/nmap. Anyway, cSploit has become the most powerful network security exploiting (mobile penetration testing) application on mobile device of all time. In my opinion, it may eventually force zANTI 2 to find another way out.


// Main Applications //
- Map your local network
- Enumerate local hosts
- Fingerprint hosts’ operating systems and open ports
- Find vulnerabilities
- Find exploits for these vulnerabilities
- Use those exploits to gain access to the target
- Crack wifi passwords
- Install backdoors for later access
// Main MitM Attacks //
- Image, text, and video replacement– replace your own content on unencrypted web pages
- JavaScript injection– add your own javascript to unencrypted web pages.
- password sniffing ( with common protocols dissection )
- Capture pcap network traffic files
- Real time traffic manipulation to replace images/text/inject into web pages
- DNS spoofing to redirect traffic to different domain
- Break existing connections
- Redirect traffic to another address
- Session Hijacking– listen for unencrypted cookies and clone them to take Web session
// System Requirements //
- Android 2.3+
- Root privilege required
- You have to completely install BusyBox, including its all components
- SuperSU required
// Fan Made Demo Video //
https://www.youtube.com/watch?v=UVhXshriZM8
// Installation Notes //
- First of all, root your Android OS using SuperSU (if required). Otherwise, you will see error like this:
- Initialization Error: cannot find a core for this device
- Core is not installed, the application will just check for updates…
- Fatal error…
- Download and install BusyBox, cSploit
- Run BusyBox first, then run cSploit
- Follow the instructions to continue…
// Related Links //
- Use cSploit to get root shell on Metasploitable2
- Use cSploit for simple Man-in-the-Middle (MITM security demos
// Download URLs //
| Stable/Pre Release | Nightly Build |
 |
 |
| If some download link is missing, and you do need it, just please send an email (along with post link and missing link) to remind us to reupload the missing file for you. And, give us some time to respond. | |
| If there is a password for an archive, it should be "appnee.com". | |
| Most of the reserved downloads (including the 32-bit version) can be requested to reupload via email. |