| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |
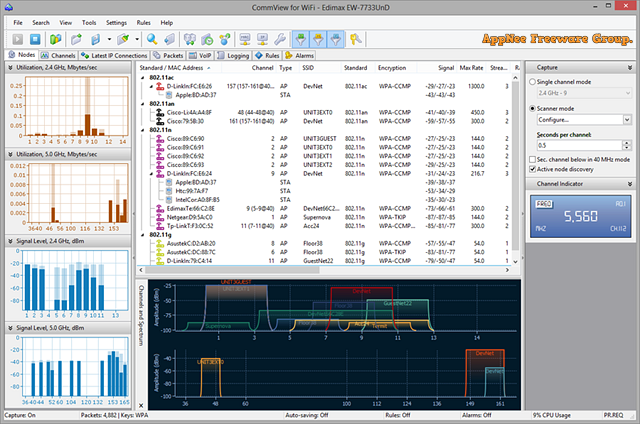
I think readers who understand wireless network well know that the security of wireless network comes with congenital deficiency – i.e.: the wireless signal is easy to leak. As a result, compared with the wired network, the monitoring action made to wireless network signals is much easier. CommView for WiFi is a powerful wireless network monitor and analyzer (i.e.: packets capturing and monitoring tool) with friendly UI, industry-leading performance, good flexibility and usability. It’s specially developed (by TamoSoft from New Zealand) for wireless network administrators, security specialists, network programmers, or anyone wanting to understand the wireless network communication clearly.
Continue reading [v7.0, v7.3] CommView – Powerful wireless network monitor and analyzer