| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |
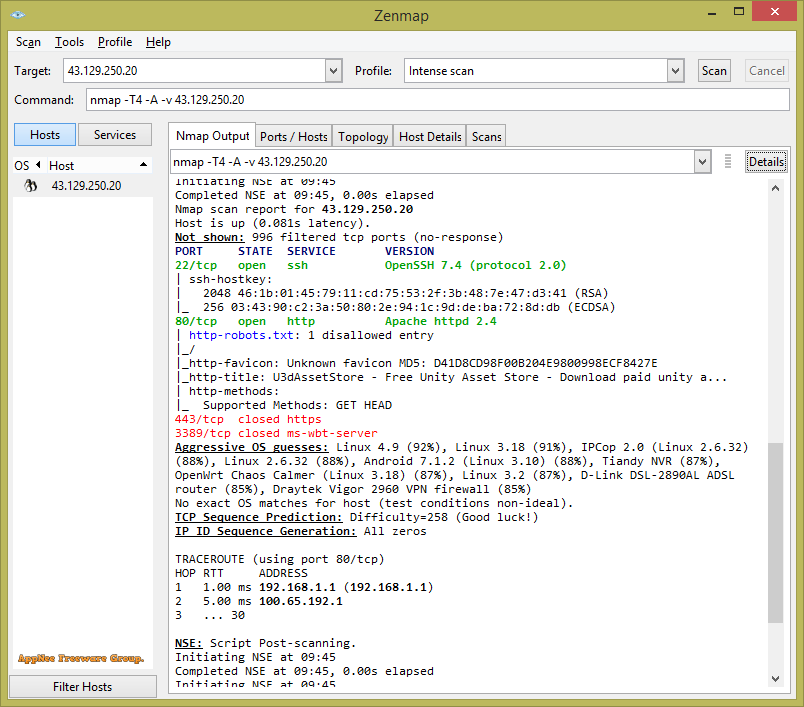
Nmap (short for Network Mapper) is a free and open-source network security scanner for large networks. It was originally developed by Gordon Lyon (Fyodor Vaskovich) for Linux in 1997, later gradually became one of the most popular network discovery and security auditing tools on multiple operating systems with the participation of many volunteers in the open source community.
By sending packets and analyzing the responses, Nmap can detect whether the target host is online, operating system used, open port, network service running, packet filter/firewall used, as well as version information, device type, reverse domain name, MAC address and a bunch of other information. In addition, it allows the use of scripts to extend functionality, and can adapt to network conditions including latency and congestion during a scan.
As one of the necessary tools for network security auditing, system and network administrators can use Nmap to do some daily operation and maintenance work, such as viewing the information of the entire network, managing service upgrade plans, monitoring the running of hosts and services, etc. At the same time, Nmap is a favorite tool for hackers, and regarded as one of the top 10 hacking tools (port scanning edge tool). They can use Nmap to gather information about the network settings of a target computer, so as to plan an attacking method.
// Key Features //
| Feature | Description |
| Host discovery | Identifying hosts on a network. For example, listing the hosts that respond to TCP and/or ICMP requests or have a particular port open. |
| Port scanning | Enumerating the open ports on target hosts. |
| Version detection | Interrogating network services on remote devices to determine application name and version number. |
| TCP/IP stack fingerprinting | Determining the operating system and hardware characteristics of network devices based on observations of network activity of said devices. |
| Scriptable interaction with the target | Using Nmap Scripting Engine (NSE) and Lua programming language. |
// Main Applications //
- Auditing the security of a device or firewall by identifying the network connections which can be made to, or through it.
- Identifying open ports on a target host in preparation for auditing.
- Network inventory, network mapping, maintenance and asset management.
- Auditing the security of a network by identifying new servers.
- Generating traffic to hosts on a network, response analysis and response time measurement.
- Finding and exploiting vulnerabilities in a network.
- DNS queries and subdomain search.
// Related Links //
- Nmap Reference Guide
- Nmap Cheat Sheet plus Nmap + Nessus Cheat Sheet
- Nmap Cheat Sheet: Commands & Examples
// Download URLs //
| License | Version | Download | Size |
| Freeware | Latest |  |
n/a |
| If some download link is missing, and you do need it, just please send an email (along with post link and missing link) to remind us to reupload the missing file for you. And, give us some time to respond. | |
| If there is a password for an archive, it should be "appnee.com". | |
| Most of the reserved downloads (including the 32-bit version) can be requested to reupload via email. |