| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |
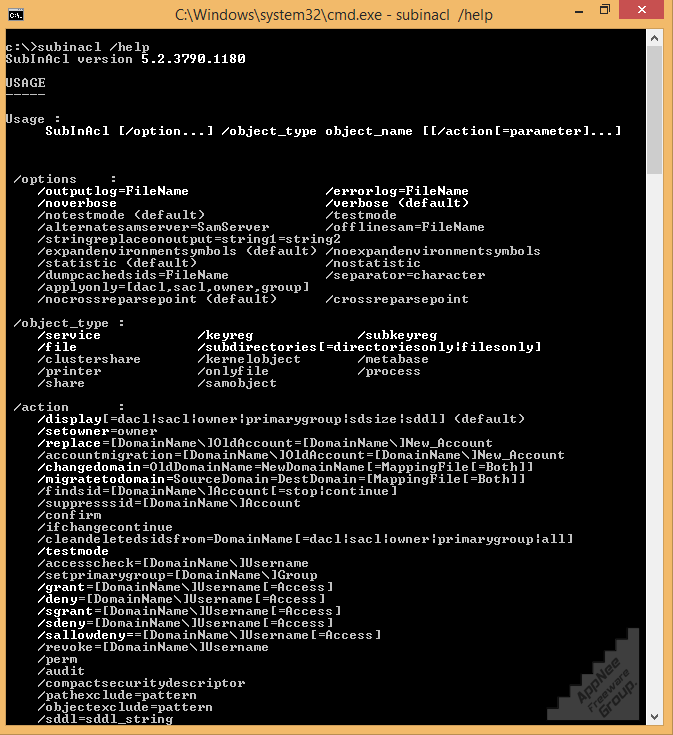
SubInACL is a tiny tool from Microsoft for performing permission management on folders, files, registries, services, and other objects. It was released as one of the tools in Windows Resource Kits. It is very powerful and practical, and much more powerful than cacls and its replacement, icacls. It is considered to be an edge tool for setting access permissions, suitable for professionals such as programmers and administrators.
When you encounter a situation where a file/folder is not accessible even to the system administrator, it is usually caused by the fact that the owner of this file/folder is not set and the permission of system administrator has been removed. The only way to access this folder or file is to set its owner to system administrator and add the full control permission of administrator. In another case, if a user does not have the administrator permission, when installing Windows service, its Start, Stop and other functions are disabled (in gray state). In cases like these, you can use SubInACL to increase/elevate the permissions of an account to solve the problem with precision.
// Key Features //
- If used properly, it does not tamper any existing permission.
- Can change permission/ owner to those subfolders where inheritance is disabled.
- Can change permission even if we do not have access to a folder/subfolder.
- Output log and error log can be enabled.
// Main Applications //
- Display security information associated with files, registry keys, or services. This information includes owner, group, permission access control list (ACL), discretionary ACL (DACL), and system ACL (SACL).
- Change the owner of an object.
- Replace the security information for one identifier (account, group, well-known security identifier (SID)) with that of another identifier.
- Migrate security information about objects. This is useful if you have reorganized a network’s domains and need to migrate the security information for files from one domain to another.
// Main Parameters //
| Parameter | Description |
| /view_mode | Specifies the amount of information to be displayed during the run. There are two quantity levels to choose from: verbose=1 or verbose=2. Default is the latter, at which point most of the information is displayed. |
| /test_mode | Indicates whether commands interact directly with the operating system when they are run or tested for successful execution. The default option is that all commands interact directly with the OS. |
| /object_type | Specifies which Windows object is executed for this operation. Optional objects include services, registry keys, registry subkeys, files, subdirectories, shares, printers, and so on. There is no default value for this parameter, but it is required. |
| /action | Specify the operations of SubInACL. The default option is to display the corresponding information for the specified object. Options include display, replace, changedomain, migratetodomain, findsid, grant, deny, revoke, accesscheck, and ifchangecontinue, and so on. |
// Some Use Examples //
| Action | Command line |
| Sets the owner of directory | subinacl /subdirectories=directoriesonly directory name\*.* /setowner=administrators |
| Sets the owner of file | subinacl /subdirectories directory name\*.* /setowner=administrators |
| Sets full control permission of directory | subinacl /subdirectories=directoriesonly directory name\*.* /grant=administrators=f |
| Sets full control permission of file | subinacl /subdirectories directory name\*.* /grant=administrators=f |
| Clears the unused user SID of the specified directory and files |
|
| Sets registry | subinacl /keyreg “HKEY_LOCAL_MACHINE\system\ControlSet001\Services” /grant=administrators=f |
| Sets folder | subinacl /file d:\ /grant=administrators=F |
| Starts mysql service with normal user | subinacl.exe /service SERVICENAME /grant=USER=f |
// Prompts //
- The most complete instructions from the official are available in the software directory.
- The installation version will automatically attach this program to the “Path” system variable of environment variables.
- Copy subinacl.exe to C:\Windows\System32, then you can use it by running “subinacl” directly in the CMD.
- Permissions for files and directories need to be set separately, they do not support extending up or down.
- It is also wise to test the changes with the “/testmode” parameter before using the tool on a running operating system.
- Run “subinacl /help /full” to see a descriptive help file, which describes the objects and operations of SubInACL, as well as how they are used in some specific circumstances.
// Related Links //
- SubInACL Online Help (by SS64)
- SubInACL Complete Tutorial (by TechNet)
// Download URLs //
| License | Version | Download | Size |
| Freeware | v5.2.3790 Final | Setup + Portable | 129 KB | 89.3 KB |
(No Homepage)
| If some download link is missing, and you do need it, just please send an email (along with post link and missing link) to remind us to reupload the missing file for you. And, give us some time to respond. | |
| If there is a password for an archive, it should be "appnee.com". | |
| Most of the reserved downloads (including the 32-bit version) can be requested to reupload via email. |