| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |
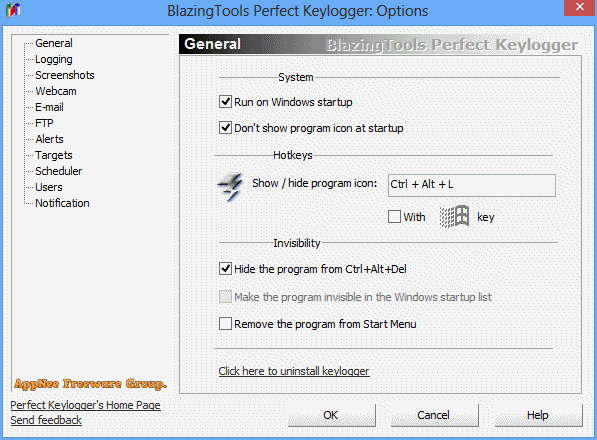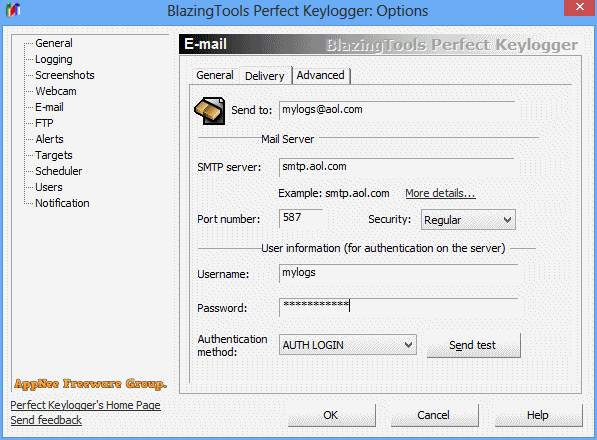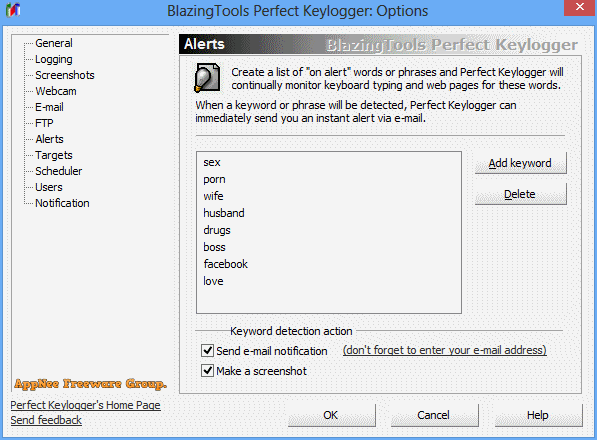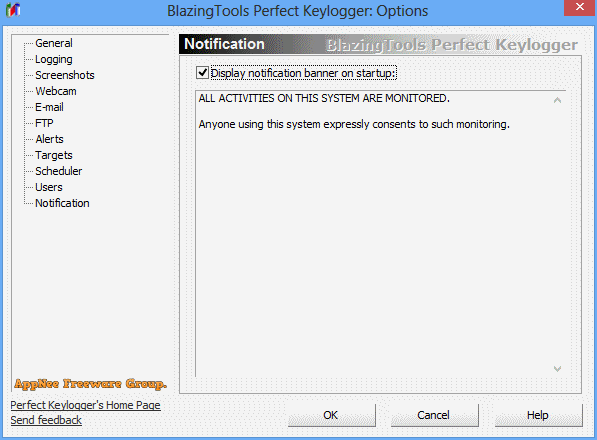
Perfect Keylogger is an excellent keyboard logger created as an alternative to the very expensive commercial products such as iSpyNOW, Spector Pro, eBlaster. It has similar functionality, but is easier to use. Because it hides the complex internal mechanisms behind a user-friendly interface. It is also the first keylogger software solution that can be completely invisible in Windows Task Manager.
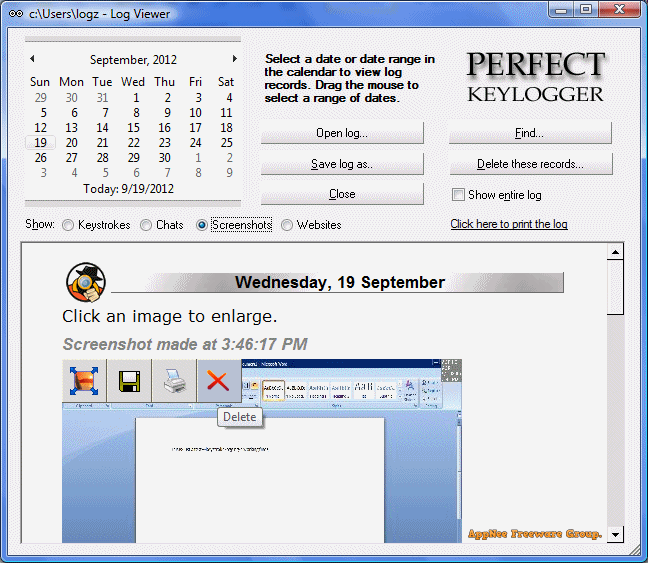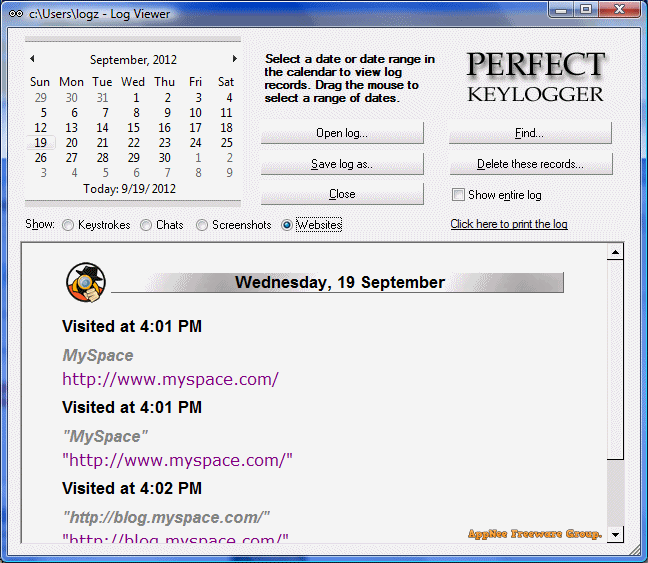
Perfect Keylogger logs all user activities on the computer, such as keyboard inputs, programs launched, windows opened, websites/pages visited; supports periodic screen capture; has advanced keyword detection and notification functions; can bundle other software and generate the installation package file; can completely hide itself in the taskbar or even in the Task Manager (no button, icon, or process displayed), and run completely in secret.
Perfect Keylogger can work in absolute stealth mode, and is almost undetectable. The hidden mode means that there are no buttons or icons in the taskbar, and no task/process information is displayed in the Task Manager. Of course, unlike spyware products, Perfect Keylogger doesn’t send any information to the software developer. Instead, only you receive and view the log files, thus ensuring absolute privacy.
Installing Perfect Keylogger on your own PC is for defensive purposes, so that you can see who touched your computer and what they did while you were away; while installing it on someone else’s computer is a spying activity. If it’s your child, you can monitor their online behaviors to protect them from the erosion of bad Internet information; If it’s a friend, it might be a prank; If they are employee, you can prevent them from slacking off or doing things that are not related to work; But if it’s a spouse, a colleague, or a stranger, you’d better do it just to find out the truth.
// Key Features //
- Has an intuitive interface and very easy to use, even for beginners
- Absolutely invisible mode
- Remote Installation / Update / Removal
- Logs texts and passwords typed in the every application, including popular instant messengers
- Supports Windows 10 / 8 Modern UI interface
- Full support of Windows 10
- Supports virtually all input languages (Unicode engine), including Japanese, Arabic, Thai, Chinese!
- Visual surveillance (screenshots)
- Multi-monitor support
- Slideshow for screenshots
- Records Webcam snapshots
- Captures passwords behind the asterisks
- Captures button clicks
- Captures screen information on every mouse click
- Logs websites visited
- Captures both sides of chats for the most popular instant messengers (Skype, MSN/Live, AIM, Yahoo and others)!
- Detection and notification of the custom keywords (alerts)
- Records contents of password protected web pages, including Web Mail messages (using our additional software)
- Monitors Windows Clipboard
- Sends text logs by e-mail (in the stealth mode)
- Sends screenshots by e-mail (in the stealth mode)
- Uploads ALL logs to separate folders by FTP (in the stealth mode)!
- Optional ZIP compression and password protection of the log files before transferring by email or FTP
- Automated renaming of the keylogger’s files and registry entries
- Monitors computer activity only when user goes online (option)
- Invisible in Windows startup list
- Monitors all users of the PC, even if you don’t know their passwords
- User friendly HTML file format for emailed logs
- Invisible in Windows Task Manager
- “Quick Install” – configure keylogger on your PC, then just run it on another PC to install
- Intercepts DOS-box and Java-chat keystrokes
- Instant install from a memory card or a flash drive
- Supports international keyboards
- External log viewer
- Supports for printing of the log
- Windows 10/8/7/Vista 64 bit support
- Strong encryption of the log file
- Records keystrokes in the specified applications
- Saves log files to HTML
// Official Demo Video //
// Universal Registration Codes //
| For | Name | Registration code |
| v1.x.x | MAX08 | SRFM-RDSR-LOBA-JWLI |
// Edition Statement //
AppNee provides the Perfect Keylogger multilingual full installers and all versions universal registration codes for Windows 32-bit & 64-bit.
// Installation Notes //
for v1.x.x:
- Download and install the latest version of Perfect Keylogger from official site
- Launch program, and click ‘Enter registration code…‘
- Use the universal registration code above to register
- Done
// Warning //
The official install files might be falsely reported as Win32:Malware-gen, Win32:Trojan-gen threat with high risk. Use VirusTotal to make a full, authoritative scan, and decide to use it or not by yourself.
*** Please remember: antivirus software is not always right, just be careful and use it at your own risk.
// Related Links //
// Download URLs //
| Version | Download | Size |
| Latest |  |
n/a |
(Homepage)
| If some download link is missing, and you do need it, just please send an email (along with post link and missing link) to remind us to reupload the missing file for you. And, give us some time to respond. | |
| If there is a password for an archive, it should be "appnee.com". | |
| Most of the reserved downloads (including the 32-bit version) can be requested to reupload via email. |