| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |
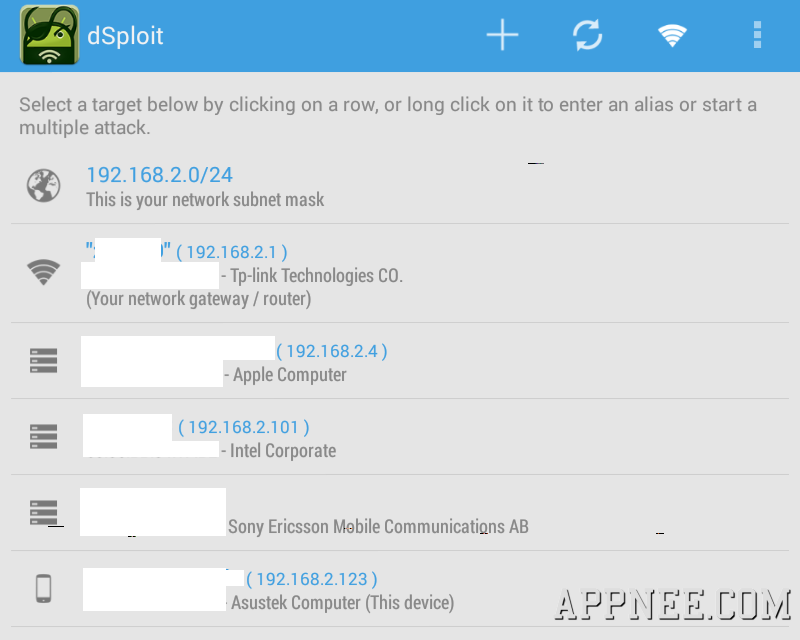
With the development of mobile devices and network, intelligent mobile phone has become a new paradise for hackers. Imagine, under this environment of everybody holds a smart phone nowadays, nothing is more active than the mobile phone viruses and the vulnerabilities’ exploits of software and mobile network. Therefore, to understand and master some practical security tools seems necessary and meaningful.
Continue reading [v1.1.3c] dSploit – Most popular penetration testing suite for Android




