| Ⅰ | This article along with all titles and tags are the original content of AppNee. All rights reserved. To repost or reproduce, you must add an explicit footnote along with the URL to this article! |
| Ⅱ | Any manual or automated whole-website collecting/crawling behaviors are strictly prohibited. |
| Ⅲ | Any resources shared on AppNee are limited to personal study and research only, any form of commercial behaviors are strictly prohibited. Otherwise, you may receive a variety of copyright complaints and have to deal with them by yourself. |
| Ⅳ | Before using (especially downloading) any resources shared by AppNee, please first go to read our F.A.Q. page more or less. Otherwise, please bear all the consequences by yourself. |
| This work is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License. |

HOIC (AKA: H.O.I.C., short for High Orbit Ion Cannon) is a free and open-source network stress testing and DoS/DDoS attacking application for Windows, Mac and Linux. It was written in Visual Basic and C#, developed by Anonymous (a hacktivist collective) during the Operation Payback after federal agents shut down Megaupload, and released as LOIC‘s predecessor.
HOIC was designed to replace Praetox Technologies’ LOIC, because LOIC is not powerful enough to launch attacks with such a limited number of users. By contrast, HOIC functions by flooding target systems with junk HTTP GET and POST requests (i.e.: HTTP Flood), and is able to attack as many as 256 URLs/domains at the same time. Even better, it has the ability to cause an HTTP Flood with as few as 50 user agents being required to successfully launch an attack, and the coordination between multiple users leading to an exponential increase in the damage. That’s why HOIC is regarded as one of the most versatile tools for hackers who are attempting to co-ordinate DDoS attacks as a group.
Among all similar tools, HOIC is the first one to support the so-called “booster file” with .hoic extension, which follows VB 6 and VB .NET syntax, and is responsible for defining the dynamic request attributes, launching attacks on multiple pages within the same website, greatly increasing the attack magnitude, and helping evade some defense filters. It works as a configurable VBScript module that randomizes the HTTP headers of attacking computers, thus allowing thousands of highly randomized combinations for user agents. That is, the booster also lets HOIC users customize the application and randomize the assaults in order to circumvent caching mechanisms that protect servers from traffic spikes.
In addition to the booster scripts, many HOIC users also use Swedish proxies to obfuscate their location, because it is believed that Sweden has more strict/secure internet privacy laws. Furthermore, anonymizing networks such as TOR are not capable of handling the bandwidth of attacks generated by HOIC. Any attempt to launch an attack using the TOR network will actually harm the network itself. And, HOIC is undoubtedly used in many malicious and illegal attacks, but it is still legally available on the Internet, because it has applications as a legitimate testing tool for users who want to implement an effective “stress test” on their own networks.
One limitation of HOIC is that it requires a coordinated group of users to ensure that the attacks are successful. Even though it has allowed attacks to be launched by far fewer users than LOIC, HOIC still requires a minimum of 50 users to launch an effective attack and more are required to sustain it if the target website employs security protection measure. Another limitation is the lack of anonymizing and randomizing capabilities. Even though HOIC offers anonymizing through the use of booster files in theory, the actual protection provided is not enough yet.
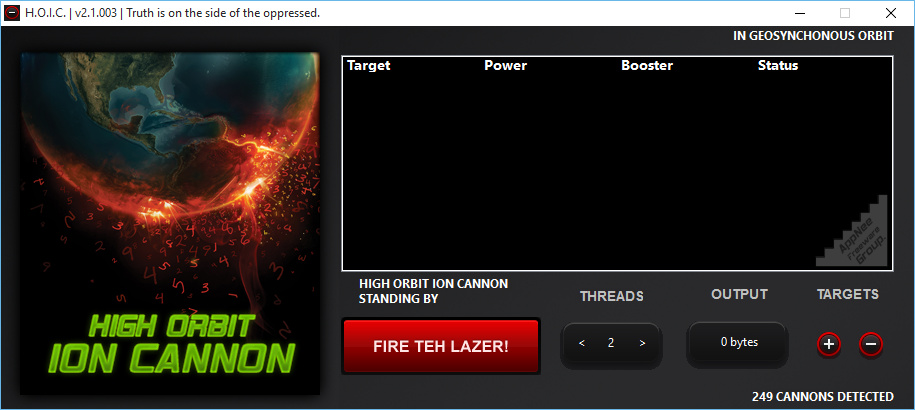
// Key Features //
- High-speed multi-threaded HTTP Flood
- Simultaneously flood up to 256 websites at once
- Built in scripting system to allow the deployment of ‘boosters’, scripts designed to thwart DDoS counter measures and increase DoS output
- Easy to use interface
- Can be ported over to Linux/Mac with a few bug fixes (I do not have either systems)
- Ability to select the number of threads in an ongoing attack
- Ability to throttle attacks individually with three settings: LOW, MEDIUM, and HIGH
// Power Option //
The power option sets the request velocity:
- Low – at 2 requests per second
- Medium – at 4 requests per second
- High – at 8 requests per second
// LOIC Flaws //
| Flaw | Description |
| Detection | HOIC uses booster scripts that let perpetrators scatter attack traffic and hide their geolocation. This differs from LOIC, which isn’t capable of obfuscating attacker IP addresses. |
| Firepower | An individual HOIC user can launch a significant number of junk requests at a given time; as few as 50 perpetrators can execute a successful DDoS attack. This differs from LOIC, which requires thousands of users to coordinate and launch an attack. |
// How to defend against HOIC attack //
Several strategies exist to mitigate HTTP flood attacks from the HOIC:
- IP Reputation Filtering (IPRF) – a preventative measure that checks incoming IP addresses against databases of known malicious IP addresses and keeps their traffic off the network.
- A Web Application Firewall (WAF) – can set rate-limiting rules which will drop traffic from IP addresses that are making suspicious amounts of requests.
- CAPTCHA verification – test if a web client is legitimate.
- A more sophisticated method – asks web browsers to solve a simple math problem without interrupting the user experience.
// Prompts //
- The attack traffic amount generated by one HOIC user is still not enough at all to take down a target system. In other words, a successful DDoS attack can only be launched when a team of cooperators operate HOIC simultaneously.
// Warning //
This program might be reported as Win32:PUP-gen [PUP] threat with high risk. Use VirusTotal to make a full, authoritative scan, and decide to use it or not by yourself.
*** Please remember: antivirus software is not always right, just be careful and use it at your own risk.
// Download URLs //
| License | Version | Download | Size |
| Freeware | Latest |  (mir) (mir) |
n/a |
(Homepage)
| If some download link is missing, and you do need it, just please send an email (along with post link and missing link) to remind us to reupload the missing file for you. And, give us some time to respond. | |
| If there is a password for an archive, it should be "appnee.com". | |
| Most of the reserved downloads (including the 32-bit version) can be requested to reupload via email. |